A question raised recently in a Reddit security discussion described something most security teams recognise immediately, even if they don’t always say it out loud.
An HR team needed to send employee enrolment data to insurers, banks, and benefits providers. Full names, Social Security numbers, dates of birth, dependent details. Security blocked the transfer because policy clearly forbids sending this class of data by email, even if it’s encrypted. HR pushed back and said they had no choice, the vendors only accept the data by email.
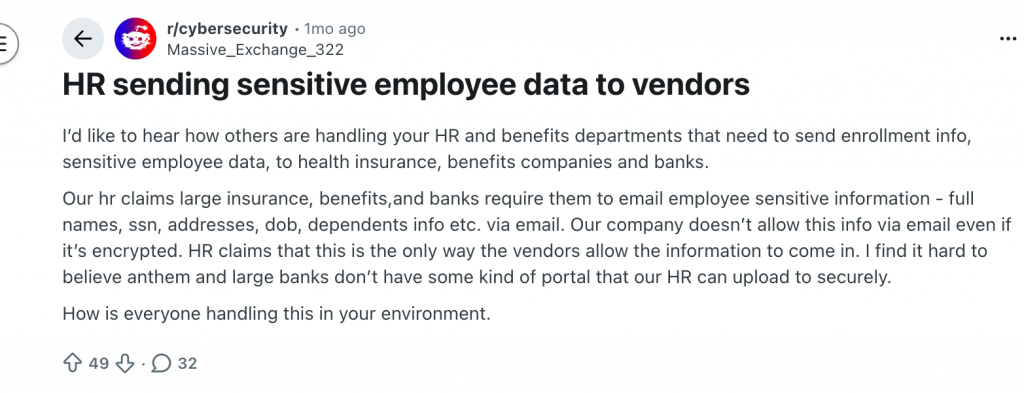
Photo Credit: Reddit
This didn’t sit right with a lot of people. The replies came from security practitioners, auditors, third-party risk teams, and people who had worked inside banks and insurance companies. Their reactions were the same; this situation is common, it’s frustrating, and in most cases, it’s avoidable.
Several contributors to the discussion pointed out something that should not be controversial. Large insurers, banks, payroll providers, and benefits platforms already have secure ways to receive sensitive data so email is not the requirement, instead it’s the path of least resistance.
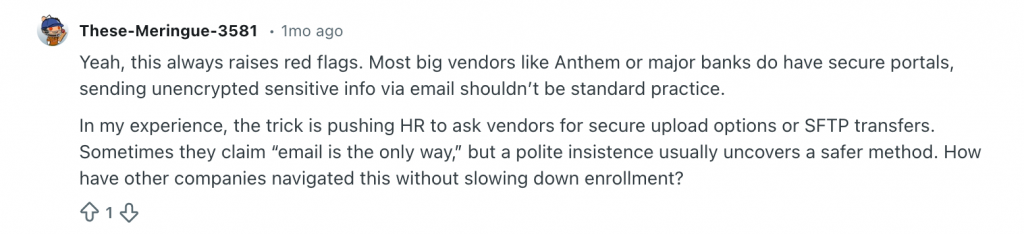
Photo Credit: Reddit
I think the real issue here is convenience. Once a process becomes “how it’s always been done,” the risk fades into the background; HR just wants enrolment completed on time, vendors accept the files because no one challenges the process and ends up stuck in the middle, enforcing policy while being told they’re blocking the business.
Someone stated that a good approach is to assess the risk, force a different procedure and have senior leadership sign off on a risk exception if they feel otherwise. Without adopting any of these approaches, anything else is silent acceptance, and silent acceptance is still acceptance.
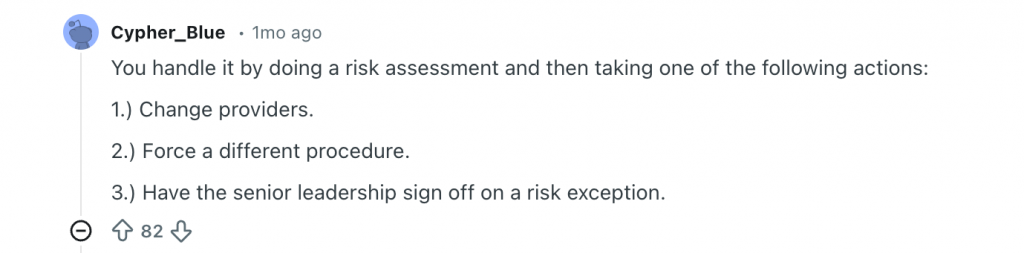
Photo Credit: Reddit
Managing sensitive employee data is not only HR’s responsibility and the security department must establish minimum standards and enforce compliance across the organisation and HR on their end must follow these standards, regardless of convenience.
If a vendor truly cannot accept employee data securely, that is a serious signal. And if leadership still chooses to proceed, that risk should be explicit, documented, and owned at the executive level. Quiet exceptions and “temporary” workarounds are how unsafe practices become permanent and how breaches become inevitable.
The frustration in that thread was not about being difficult or obstructive. It was about responsibility and that distinction matters.

