Nothing is safe in this digital world. Every other day, we read about hacking attempts and security threats. Since our whole life is becoming online, the number of black-hat hackers is also increasing. Hackers are now using different techniques to break into your banking accounts.
There are multiple ways a hacker could hack your banking accounts. So, if you use internet banking services, then you need to follow some security steps to safeguard your banking accounts.
6 Methods Hackers Use To Hack Your Bank Accounts
In this article, we would share a few popular methods hackers use to hack your bank accounts. By knowing the techniques, you will be in a better situation to understand how your accounts can get hacked. So, let’s check out the methods hackers use to break into your bank account.
1. Banking Trojans (Smartphones)

Source:https://www.prosyscom.tech
Hackers can use malicious apps to break into their banking accounts. In this method, hackers create a duplicate copy of a legitimate banking app and upload it to third-party app stores. Once downloaded, the app sends the username and password to the creator.
2. App Hijacking
In this method, a hacker creates a fake trojan-filled banking app. When installed, it sits silently in the background and scans your phone for a banking app. When it detects a banking app, it shows a fake window that looks identical to the legitimate banking app and drives you to the login page.
Source:https://www.techviral.net
The process is done so smoothly that a regular user won’t even notice the swap and will end up entering the details on the fake login page.
3. Smishing
Smishing is an SMS version of Phishing. It’s a scam in which hackers uses SMS instead of email templates to lure recipients into providing credential via text message reply.

Source:https://www.hoax-slayer.net
Smishing scams might show themselves as a request from the bank, a note from the company, a lottery prize, etc. Every template will ask you to make a payment by entering the credit/debit card details.
4. Keyloggers
Keyloggers are another popular hacking technique used by hackers. Keyloggers are of two types – hardware and software. The software versions need installation. Once installed, it silently records your keystrokes and sends the information back to the hacker.

Source:https://www.techquark.com/
The hardware keyloggers need to be fitted into the line from a keyboard to a device. Hardware keyloggers need to be installed physically on the device. Once established, it serves as a software keylogger.
5. SIM Swapping
Source:https://www.thehackernews.com
SIM swapping is one of the rare techniques that hackers can use to break into your bank account. In this method, the hacker contacts your mobile network provider, claiming to be you. They convince network providers to assign the registered phone number to a new card.
If they are successful in doing so, all incoming calls and SMS will be routed to the new SIM card. It might look harmless and unachievable at first glance, but if done correctly, it can cause lots of harm. It can hack almost every accounts linked with a phone number.
6. Man-in-the-middle attack
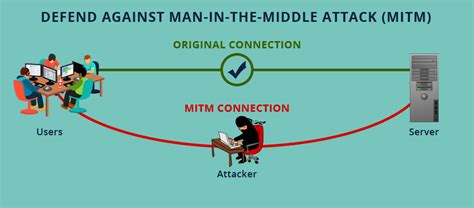
Source:https://style.tribunnews.com
The man-in-the-middle attack is one of the most dangerous hacking techniques used by hackers. In a Man-in-the-middle attack, the hacker inserts him/herself into a conversation between two parties. In the banking section, the two parties will be the user and the banking application.
However, it’s an advanced technique that requires monitoring an insecure server and analyzing the data that it passes through. The ultimate goal of this attack is to steal sensitive information like banking credentials, credit card details, etc.
Conclusion
These are six methods hackers use to break into your bank account. Please endeavor to protect your banking information from silent walkers. We hope this article helped you! Share it with your loved ones as well.

